CVE-2024-37389 — Apache NiFi Improper Neutralization of Input in Parameter Context Description
Apache NiFi 1.10.0 through 1.26.0 and 2.0.0-M1 through 2.0.0-M3 support a description field in the Parameter Context configuration that is vulnerable to cross-site scripting. An authenticated user, authorized to configure a Parameter Context, can enter arbitrary JavaScript code, which the client browser will execute within the session context of the authenticated user. Upgrading to Apache NiFi 1.27.0 or 2.0.0-M4 is the recommended mitigation.
This issue is being tracked as NIFI-13374
Proof of Concepts
Apache NiFi allows users to add comments to a Parameter Context. However, the input for this comments was not properly sanitized, leading to a Cross-Site Scripting (XSS) vulnerability. This could allow malicious users to inject and execute arbitrary scripts, posing significant security risks.
- Create a new Parameter Context with XSS payload in the comment section.
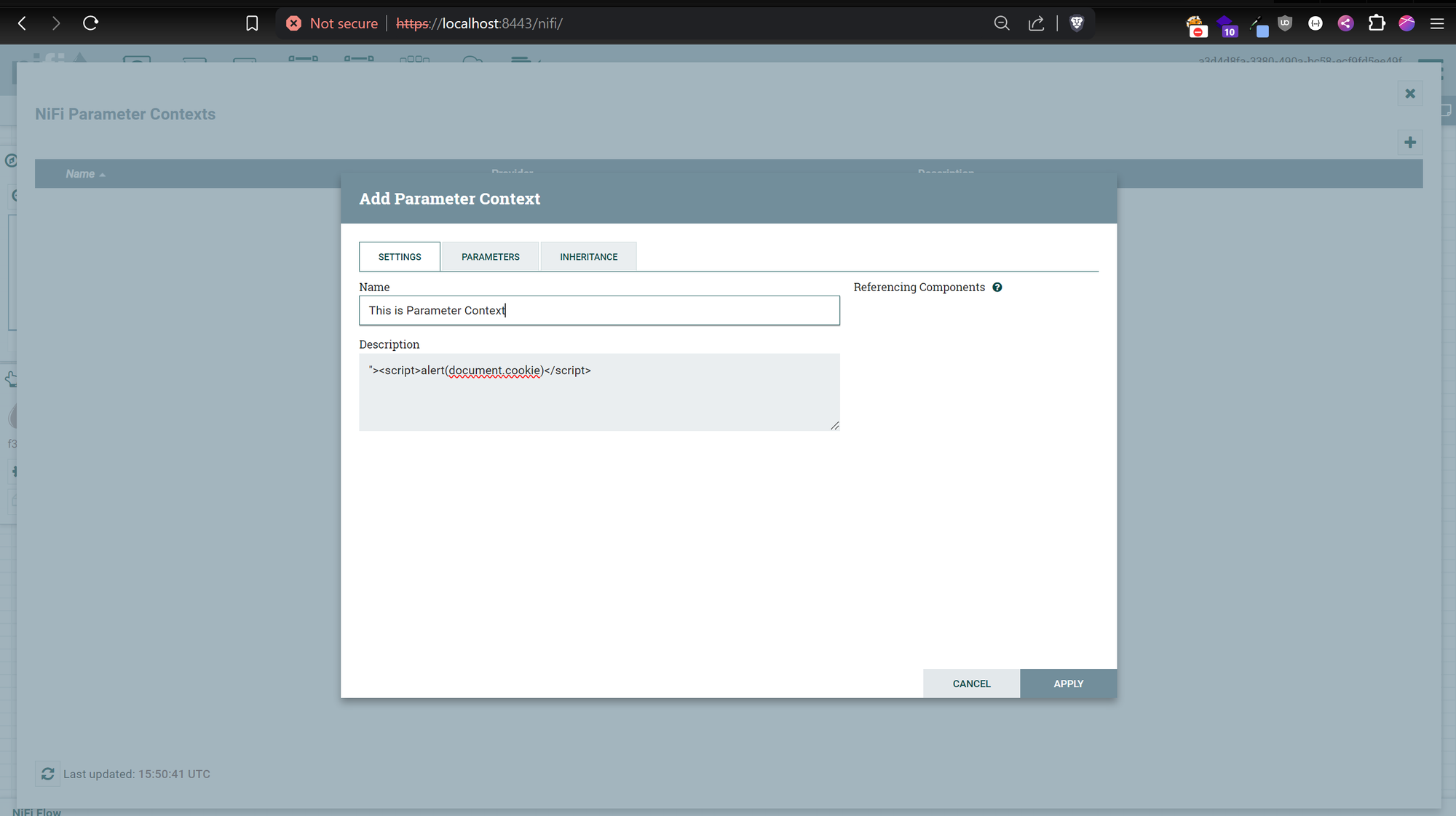
- Create a new Process Group. While the popup shows, hover the cursor to the “?” icon to trigger XSS.
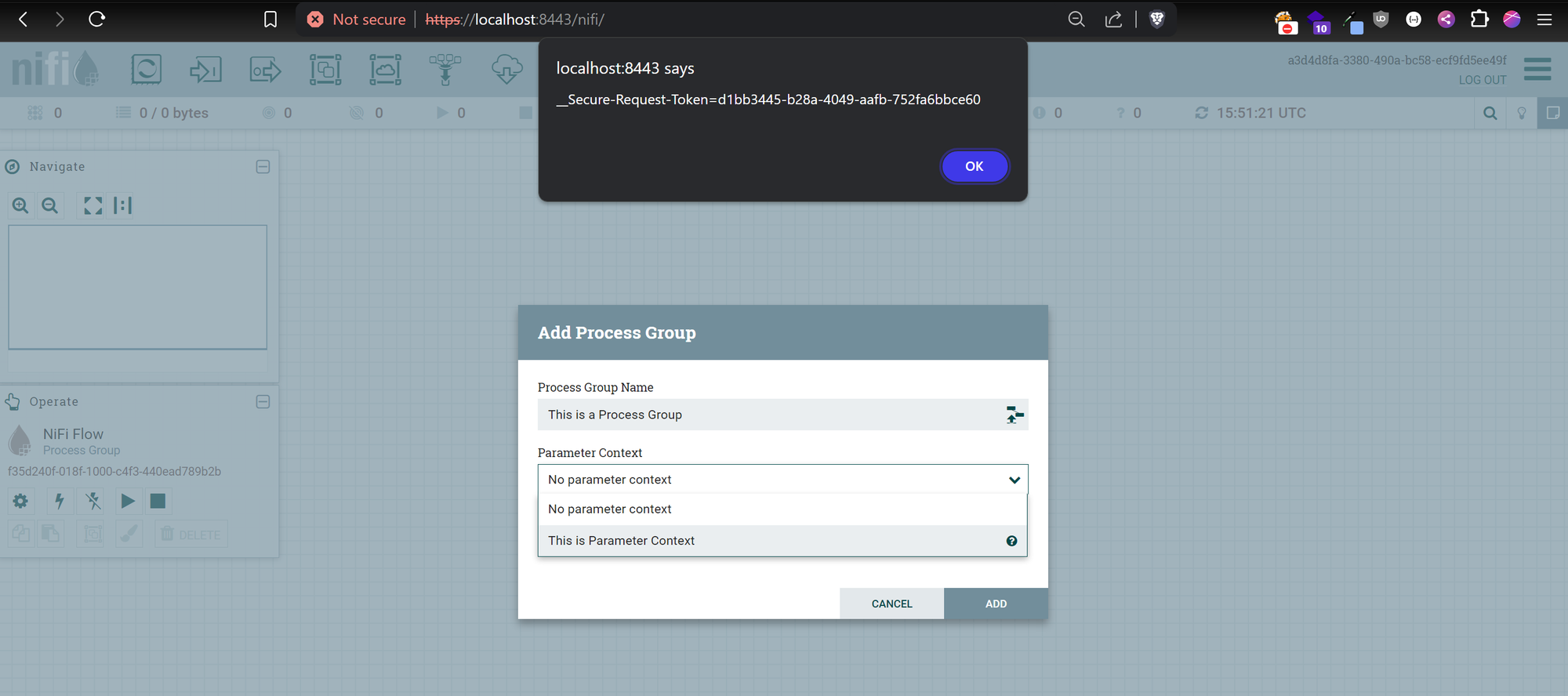
XSS Payload will triggered once you hover in the ? icon for description in tooltip.
Impact
An authenticated user, authorized to configure a Parameter Context, can enter arbitrary JavaScript code, which the client browser will execute within the session context of the authenticated user.